The Next Evolution in Symantec Access Management
How do you leverage data protection risk signals within your access management platform?
I recently read a blog from a colleague about the importance of Identity and Access Management as the cornerstone for implementing a Zero Trust architecture, and there were two sentences that really struck a chord. The first was, “Identity is the last (and sometimes only) defensible perimeter” and the second was the need to move to a “pro-active observe --> detect --> prevent approach...to be a lot more agile in preventing risky identities from causing significant damage.”
These stuck out because I have also been exploring ways to improve our own session management capabilities and examining the recent progress made within the standards bodies to accomplish the same goal. But before we get into the details on both fronts, let’s consider where we used to be and why we need to evolve.
Continuous Authentication/Verification in the Time of Cookies
The concept of continuous authentication is not new. For over twenty five years SiteMinder has been securing online resources. From the user’s perspective, they authenticated once and then had seamless access to their resources, but in the backend, the session management capabilities of SiteMinder were continuously verifying their identity before granting access. And the bulk of this data was stored within the SMSESSION cookie, a proprietary mechanism used for session management. So, if we solved this problem years ago, why the need to change?
Part of the answer lies in the evolution of the underlying IT technology stack, including apps and data running outside of any defined security perimeter. But at the end of the day we are still dealing with claims based tokens being used to validate access to a resource. What is more significant, is the rise in cyber-attacks based on the opportunities presented by this perimeter-less architecture and the need to move from the existing point-in-time access checks to a continuous process that leverages real-time risk signals from a range of sources to significantly improve how we determine whether or not to grant access and also when to revoke that access.
The Rise of the Machine and Behavioral Analytics
Finance was one of the first sectors to pioneer the use of User and Entity Behaviour Analytics (UEBA) within the authentication and authorization process to implement stronger authentication mechanisms for online banking. The Broadcom Payment Security Division actually partnered with leading credit card providers to develop the first 3D-Secure specification to secure online credit card transactions, which leverage contextual risk models to help prevent fraudulent transactions. This same risk technology is also incorporated within our IAM solution, allowing it to capture historic usage and behavior data, and compare this data against real-time time data collected during authentication. This has proven to be very effective in helping enterprises balance when they apply stronger authentication mechanisms to their users (that is, just when higher risk is detected). And, while this has been very effective, it has been recognized that more data is needed to further improve upon this type of analysis. The challenge now is identifying what types of data to collect and from where?
A Standards-based Approach to Risk Management
Earlier access management technologies all implemented session management through a proprietary mechanism. This was done not just to make them more secure, but also because in many cases, these systems were solely responsible for managing authentication, authorization, and auditing for the protected online resources. But over time as these services became distributed over many types of technologies and were delivered as discrete services, the need for formal standards to handle these types of communications became apparent. SAML was the first identity standard, but this was eclipsed by OpenID Connect (OIDC), and it is within the OpenID foundation that improving interoperability for session management has really taken off.
One initiative, pioneered by Google, is the Continuous Access Evaluation Protocol (CAEP), which focuses on sharing events that relate to changes in access profile over time such as network connection, user behavior and other related risk context. This information can then be used to communicate adjustments to authentication controls over the life of a session as the context for the session changes. CAEP has since been merged with a similar initiative called Risk & Incident Sharing and Collaboration (RISC), under the Shared Signals and Events (SSE) working group within the OpenID Foundation. RISC focused on sharing events that can enable providers to prevent attackers from compromising linked accounts. For example when social login is used to authenticate to a variety of cloud services, any compromise to the account should be immediately communicated to all providers.
Symantec, as a division of Broadcom, has numerous security technologies to address the various pillars of Zero Trust, but bringing these components together to deliver premium threat protection for our customers is where we bring the most value.
The main difference between what the SSE is doing and standard OIDC session management is that the SSE is more concerned with detailed aspects of session state changes, whereas OIDC simply supports single logout. The SSE is also looking at a broader set of data that could be leveraged, ranging from suspicious activity detected in endpoint solutions, firewalls, or proxies (such as CASB technologies); effectively any technology that can detect risky behavior and share that information.
But standards themselves don’t necessarily result in changes. As mentioned earlier, the primary catalyst for why this topic is important now is that migration of data and applications to the cloud has reached critical mass for many organizations. And this is raising the priority and demand for the continuous sharing of detailed session state and user/device risk context in order for Zero Trust frameworks to adapt. In other words, enterprises need to move forward now, adding continuous evaluation to their access management flows and evolve along with the standards.
How Symantec can Advance Your Efforts to Achieve Continuous Authentication
Symantec, as a division of Broadcom, has numerous security technologies to address the various pillars of Zero Trust, but bringing these components together to deliver premium threat protection for our customers is where we bring the most value. For example, let us consider our conversation to this point and the question we posed at the very beginning – how to leverage data protection risk signals within your access management platform?
Thanks to the efforts of the SSE working group, the mechanism for sharing these risk signals between interested systems is already well defined and gaining industry wide adoption. Our focus was to find a rich source of risk data that could be ingested to improve access decisioning beyond the traditional device fingerprint/geolocation changes. To this end, we used our Identity Fabric platform (VIP Authentication Hub) to integrate risk context from Symantec DLP into the access controls provided by Symantec SiteMinder using the relevant standards from the OpenID foundation to perform continuous risk-based access evaluation and session management and to greatly mitigate the risk associated with identity theft.
The diagram below shows conceptually how this works. And given the services provided by VIP Authentication Hub to enable this integration are standards based, it would not be difficult to expand this model to include risk context from other Symantec solutions or indeed similar standards compliant solutions from third-parties.
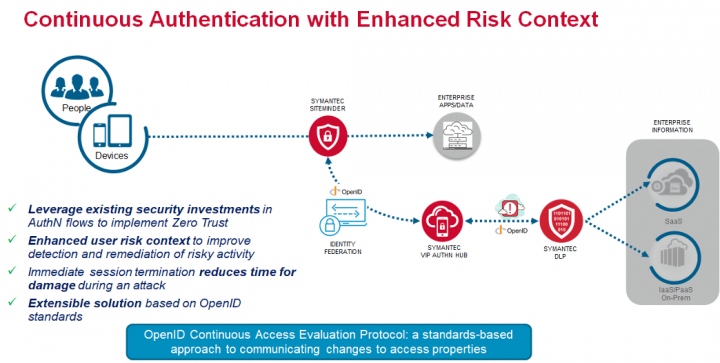
Thanks to the policy engine within VIP Authentication Hub, the process to configure this is fairly simple. When users attempt to access a SiteMinder protected resource, they are directed to VIP for part or all of the authentication process using Identity Federation. VIP collects risk signals from the DLP solution to use as part of the risk assessment and based on the result can either allow the request prompt the user for additional credentials or deny the access request. Once authenticated, the user is granted access to various resources covered by the session token. In the background, VIP continues to collect risk signals from DLP and if required terminates the session. At this point the user is forced to re-authenticate and if the risk level detected is high enough, will be blocked from further access until the risk incident has been resolved.
You can find a short recorded demonstration here of this in action using the following solution components:
- Symantec Siteminder 12.8.05
- Symantec VIP Authentication Hub 1.0
- Symantec DLP 15.7
- Symantec CloudSOC 3.132
Summary
With traditional security perimeters no longer a viable strategy, Identity is now possibly the only line of defense. So it seems logical that other aspects of a cyber-defense platform should provide as much user risk context as possible to the access evaluation process. And this process needs to be continuous both in adjusting authentication assurance levels to changes in risk over time as well as revoking risky sessions immediately to minimize the time-window available to exploit any compromised credentials.
The OpenID foundation along with the likes of Microsoft and Google have done a great job in setting up a framework for communicating security events related to authentication between interested parties. What is needed now is for enterprises to leverage this framework to include user risk signals from relevant parts of their security solutions into their existing authentication flows.
With the VIP Authentication Hub, we have provided a platform to do just this with an initial focus on integrating Authentication, Access Management and Data Protection to deliver continuous authentication driven by context-aware authorization.

Symantec Identity – The Missing Link
How can you implement a Zero Trust Architecture without Identity & Access Management?









We encourage you to share your thoughts on your favorite social platform.