Debunking the Benefits of Zero-Touch Activation
An additional 20 seconds of user interaction can save your organization from being the victim of a mobile security breach
There’s been a lot of talk recently about the benefits of “zero-touch” activation in the deployment of mobile security solutions in enterprise.
Zero-touch activation/enrollment in mobile refers to a process in which devices in an organization are provisioned and configured automatically by an admin, eliminating or minimizing the need for end-user interaction. If a device is enrolled in an Enterprise Mobility Management (EMM) system, admins can use zero-touch activation to streamline large-scale enterprise app rollouts. In the context of Mobile Threat Defense (MTD) solutions, the capability has been positioned as an easy way to activate security solutions on mobile devices without needing users to do anything (except open the MTD app on their device in most cases). This means end-users do not have to go through an activation process which involves more steps, such as entering credentials and approving app permissions.
Enterprise mobility teams may see zero-touch as the ideal way to deploy MTD across mobile fleets, believing that the less impact a deployment has on user workflows, the greater the adoption. This stems from the idea that “no matter how great a product is, if it’s complicated or time-consuming to implement, users won’t use it.”
While these are certainly important words to live by to ensure a good user experience, the truth is a product can’t be great at all if you don’t allow for its key functionality to be activated.
Zero-touch activation/enrollment in mobile refers to a process in which devices in an organization are provisioned and configured automatically by an admin, eliminating or minimizing the need for end-user interaction.
What the zero-touch argument fails to consider is one simple, albeit important, factor: efficacy of an MTD solution diminishes when critical permissions aren’t requested in the initial onboarding process.
What happens in zero-touch deployments in practice is that a security agent/app gets installed and starts to run on the mobile device but in a limited state. Since key permissions are not prompted, the app is not able to provide maximum protection against unwanted breach.
For example:
- Without a VPN protection permission, it can’t provide protection via secure VPN connection
- Without permission to access the device’s storage, it can’t scan files and determine their maliciousness
- Without a device admin permission, it can’t be prevented from being stopped or uninstalled by third-party apps
- Without a push notification permission, it can’t send notifications to end-users about mobile security threats
In many instances where a MTD solution has been deployed via zero-touch activation, we’ve seen that end-users will still eventually receive a prompt for permissions when greater functionality is needed. So end-user interaction will be required in any case – if not during the initial app activation, then at a later point when permissions are needed to enable certain protection actions. The idea of using zero-touch to make the product “less difficult” to deploy, then, has been quashed.
The bottom line: Enterprise mobility teams may not be getting the maximum value from their MTD solution when they choose zero-touch activation. Obtaining all necessary permission approvals at the onboarding stage ensures that you’re leveraging, from the get-go, the full gamut of detection and protection actions the solution has to offer, while increasing MTD sustainability. Think about it this way: having end-users invest an additional 20 seconds in the activation process can go a (very) long way in lowering the risk of unwanted security breaches to your organization.
How to Balance Between Good UX and Optimal Security
It doesn’t have to be one or the other. The UX team at Symantec Endpoint Protection Mobile (SEP Mobile) continuously experiments and looks at the hard data to optimize our user onboarding flow. This has allowed a successful activation process and high adoption rates – without sacrificing key functionality of the app.
Below is a short list of recommendations that have guided our permissions request flow. These are based on comprehensive research we conducted on the behavior of hundreds of thousands of SEP Mobile end-users who have had our solution running on their devices continuously for more than three years.
1. In the tradeoff between security functionality and end-user control over their mobile device, we allow admins in each organization to set the policy that best matches their needs. This means different companies can define differently the set of critical permissions they need in order to achieve the greatest value from their MTD solution.
2. We recommend requesting all needed or planned-to-be-needed permissions upfront, during the activation process. This is for two reasons:
- First, the best chance of capturing user attention and getting users to interact with an app is during the initial onboarding stage. If a user did not choose to install the app, i.e. it is pushed automatically through an EMM, they likely will not come back to it after install.
- Second, prompting permissions at a later stage may be too late to protect against certain security breaches. For example: asking for permission to install a protection VPN only after a security incident has been detected may not be effective – at that point the device may already be breached. The permissions we ask for are critical to enabling a high level of security on the device and reflect specific security policies and protection actions set by the organization.
Data showing permission approval rates from SEP Mobile end-users indicates how successful our activation sequence is on the field:
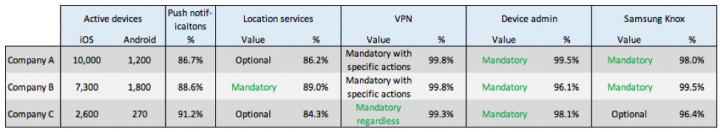
We see that an overwhelming majority of end-users accept our permissions. The notably high rates (for comparison, a 2018 survey found that the average push notification opt-in rate among US smartphone users is only 53%) indicate that even with a multi-step activation process, we have no problem getting end-users to fully-activate SEP Mobile on their devices. While zero-touch may be touted as a way to increase MTD adoption, manual activation is clearly not a reason for low adoption.
3. The line between personal and business is increasingly becoming blurred. Therefore, we make it a priority to respect the end-user's privacy preferences, even if their device is corporate-owned. To prevent any uncertainty about our app actions, we clearly explain why SEP Mobile needs each requested permission and how this information will be used, before we ask for approval.
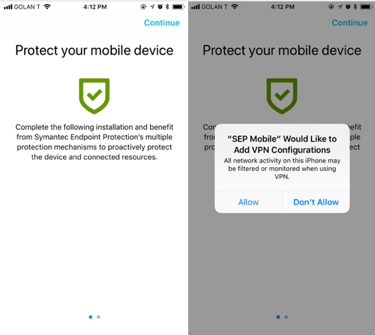
4. We always make sure to adhere to guidelines published by the mobile OS vendors.
Below is a video showing our activation process and permissions sequence on an iOS device. We believe the 30 seconds it takes to complete the process are necessary to ensure organizations get the maximum value from SEP Mobile.
When Zero-Touch Activation May Make Sense
There’s no reason to go against the grain if activation without user interaction is right for your business. This may be the case in organizations where devices are corporate owned or managed through an EMM and permissions can be automatically accepted by an admin on behalf of users.
Ultimately, we believe every organization should define the security policy and associated protection actions that best fit their needs. SEP Mobile is continuously working with customers to provide a variety of deployment methods for optimal mobile security, without impacting business.









We encourage you to share your thoughts on your favorite social platform.