Protecting Against Outlook Elevation of Privilege Escalation
Using Symantec Endpoint Security Complete (SESC) to detect and protect
Approximately ten percent of software vulnerabilities worldwide are classified as critical - meaning that there is significant cost for the systems they affect. Vulnerable systems face severe impacts to their integrity, confidentiality, and availability; all of which impair business operations and strain the security of user data. This is the case for the CVE-2023-23397 vulnerability, also known as the Microsoft Outlook Elevation of Privilege Vulnerability, made public by Microsoft on March 14th, 2023. CVE-2023-23397 is ranked as critical, based on the Common Vulnerability Scoring System (CVSS), scoring a 9.8 out of 10. This base score metric means that the vulnerability is remotely exploitable with low complexity and no user interaction required. In other words, the easier to exploit the greater the impact to the CIA triad.
Those customers who employ Symantec Endpoint Security Complete (SESC) have an added layer of security against the exploitive nature of the vulnerability, using it’s single agent for attack surface reduction, attack prevention, breach prevention, and Endpoint Detection and Response (EDR).
Through endpoint security and detection, Broadcom protects these users by mitigating, and providing visibility into the effects of CVE-2023-23397.
Symantec Endpoint Security Complete: Detection features
By analyzing CVE-2023-23397, Infolock was able to evaluate the detection and mitigation resources that customers currently have with SESC. This includes policies for endpoint and response, compliance, intrusion prevention, and firewall.
Endpoint and Response Policies: Detect WebDAV connections
If your organization blocks SMB traffic to the Internet, Windows will fall back to using WebDAV to attempt to complete the connection under an exploitive vulnerability scenario.
- An SESC Analyst can export a CSV file to analyze potential external destinations of the suspicious traffic using the following query: process.cmd_line.token:davclnt.dll,DavSetCookie.
On the Investigative tab, select the TIME, DESCRIPTION, DEVICE NAME, PROCESS COMMANDLINE, and USER columns.
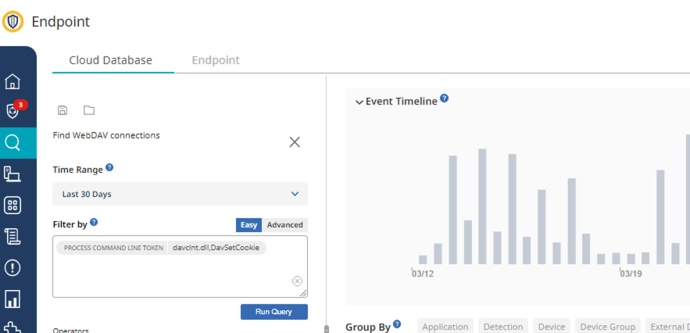
The Investigate report’s column called “Process Command Line” provides the following information that can be used as an evidence of a potential message exploiting CVE-2023-23397:
rundll32.exe C:\Windows\system32\davclnt.dll,DavSetCookie <external destination IP-FQDN> hxxp://<external destination IP-FQDN>/shared-folder/sound.wav
Host Integrity Policies (aka Compliance policy)
Host Integrity policies include custom requirements against which the compliance of the device is checked. For example, you can define a requirement to check for the existence of a Windows registry key or a registry value.
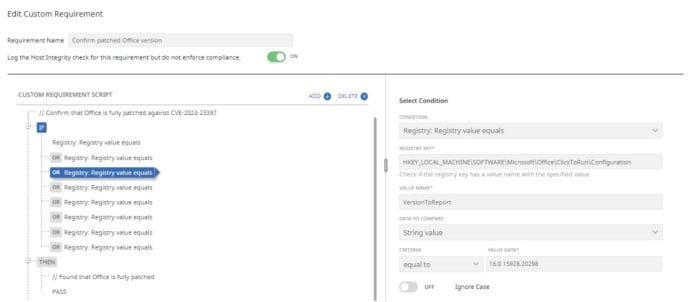
For this specific vulnerability we developed two policies: Verify if the current Office version available internally is prone to the vulnerability and how to identify indicators of compromise (IoC).
- Validate if a patched version of Outlook is deployed.
By using the Click-to-Run registry key, the Host Integrity policy can be used to determine if the specific registry value belongs to a patched Office version.
In this case, the condition to be used would be "Registry: Registry value exists." The value is based on a Click-to-Run version available at the registry.
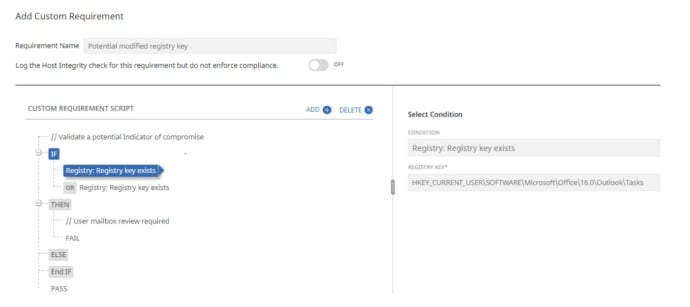
- Indicators of Compromise
The presence of specific registry keys is being analyzed as evidence that the user received a reminder for a Task or Note, under normal circumstances that registry key does not exist.
With SESC Host Integrity policy and a condition called "Registry: Registry Key exists" is possible to determine the existence of potential IoC, such as:
HKCU\Software\Microsoft\Office\<VERSION OF OUTLOOK>\Outlook\Tasks
HKCU\Software\Microsoft\Office\<VERSION OF OUTLOOK>\Outlook\Notes
Intrusion Prevention Policies
Symantec Security Response currently includes IPS signatures for two Audit detections. These are: Audit: SMBv1 NTLM Authentication Attempt and Audit: SMBv2 NTLM Authentication Attempt.
Both signatures detect NTLM authentication attempt from a private IP address to public IP, this is because Windows OS can send NTLM hashes to external host automatically when connected to them. Attackers can later use the hashes for cracking or replay attacks.
Taking into consideration that the Audit signature will just log the event, the action after the detection can be changed as required.
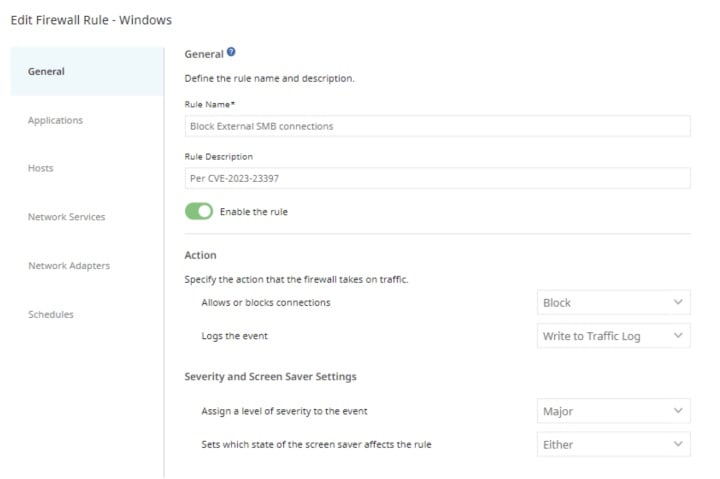
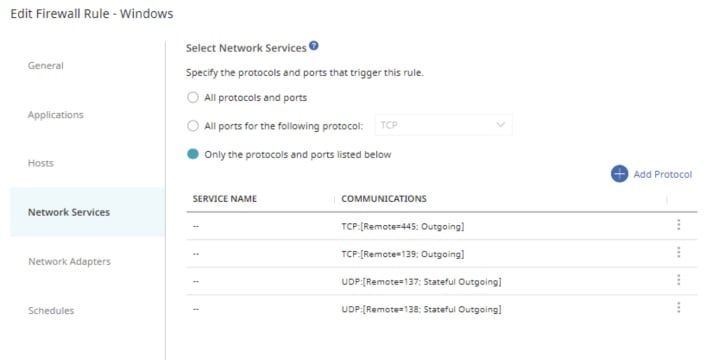
Firewall Policies
It is a general rule of thumb to block TCP 445/SMB outbound from your network as this will prevent NTLM authentication messages being sent to remote file shares.
An SESC firewall policy requires that two key Security and Network factors are established:
- Determine the internet resources that will be allowed outbound SMB connections.
- Create a required SESC Host Group from the Policy Components area to list your internal/authorized SMB connection resources.
- Determine if an external outbound SMB connection needs to be blocked or allowed with logging.
- If you have a remote worker that requires SMB traffic to a non-VPN connected resource, a log policy will help you identify risks generated on the non-VPN device.
Once the above factors are determined the firewall policy should include two rules:
- A rule to allow internal (or other authorized) SMB traffic
- A block rule to restrict outbound SMB traffic to non authorized destinations.
With almost twenty years of experience in the information security field, I have been hands-on in assisting organization in battling cyber-attacks worldwide. Working with Symantec Enterprise security solutions has allowed me to provide customers with visibility, protection, and control against security threats and to mitigate, and even prevent all together, the impact of cyber-attacks, regardless of severity level.





We encourage you to share your thoughts on your favorite social platform.