#PrintNightmare – Symantec Data Center Security Zero-Day Protection
What you should know now
(We will update this blog as more information becomes available)
Microsoft released an emergency out of band patch on July 7th for a critical remote code execution vulnerability, CVE-2021-34527 aka PrintNightmare in the Windows Print Spooler service. As of July 15th, yet another zero-day vulnerability has been announced in the Print Spooler service that allows local escalation of privilege, CVE-2021-34481. There is no patch available yet and Microsoft suggests that exploitation of the latest vulnerability by malicious actors is more likely. The third of a series of vulnerabilities within 6 weeks this year for Print Spooler, along with the vulnerabilities from 2020, CVE-2020-1048, CVE-2020-1337 referred to as PrintDemon, highlight the ongoing security risks associated with the Spooler service. Print Spooler service is enabled by default on all Windows client and server operating systems, resulting in a large population of vulnerable Windows systems regardless of whether these systems print or function as print servers.
As of July 15th, yet another zero-day vulnerability has been announced in the Print Spooler service that allows local escalation of privilege, CVE-2021-34481.
It started with CVE-2021-1675, released on June 8th, originally tagged as an escalation of privilege vulnerability. Subsequently, it was revised and bumped up in its severity to also include remote code execution. When IT admins were in the process of applying the June patch to their Windows systems, there was confusion about its efficacy as there were reports that the original June patch released for CVE-2021-1675 was not addressing the vulnerability on certain versions of Windows, in particular Windows Domain Controllers. POC exploit code got released accidentally that was used by researchers to demonstrate the impact on a fully patched Windows Domain Controller. A successful exploit allows an authenticated Windows standard user to upload a rogue DLL and remotely execute code on the Domain Controller with ‘SYSTEM’ privileges in the context of the Spooler service. An attacker could then install programs, modify data and create new accounts. Microsoft confirmed public exploitation of the zero day vulnerability via CVE-2021-34527 on July 6th and subsequently released a patch on July 7th.
Due to the high CVSS score, the recommendation is to apply the July emergency patch or the monthly update immediately. There are still some potential system configurations under which the vulnerabilities could be exploited for a local privilege escalation on a fully patched system, as confirmed by researchers using poc exploits and also documented in a CERT advisory. Microsoft has suggested additional workarounds for a true lockdown of the Spooler service. CVE-2021-34481 is still unpatched as of July 16th and has a potential for zero-day exploitation.
Symantec Data Center Security default hardening (IPS) policy provides zero-day protection for #PrintNightmare
The default lockdown offered by Symantec Data Center Security Intrusion Prevention System (IPS) for Windows systems prevents exploitation of the Print Spooler service vulnerabilities. Our coverage for various Symantec technologies is documented in our Protection bulletin. For the last 15 years, the hardened IPS policies of Symantec Critical System Protection and Data Center Security (DCS) have provided granular sandboxing controls for the Print Spooler and other Windows services. Its software install restriction prevents unauthorized and arbitrary modification of code. The figure below shows some of the sandboxing controls that hardens the Spooler service.
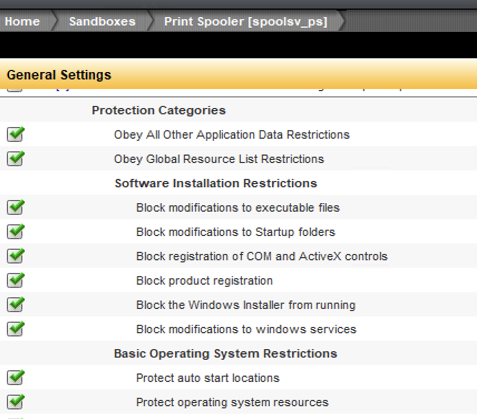
In our test of the exploit POC, DCS prevents the Spooler service from writing unauthorized DLLs to the filesystem and therefore, the compromised domain account is unable to achieve remote code execution on the DCS protected Domain Controller. Additionally, the behavior blocking policy for the Spooler service blocks suspicious processes from launching dual use tools such as cmd.exe, net.exe, rundll32.exe for malicious purposes. The application level network controls allow configuring the Print Spooler to accept inbound requests only from trusted networks.
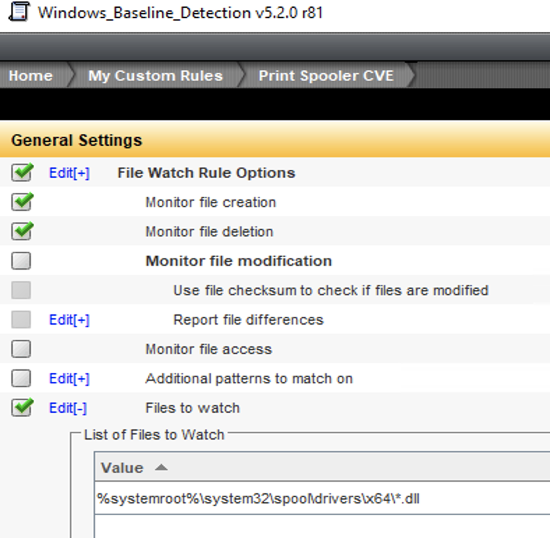
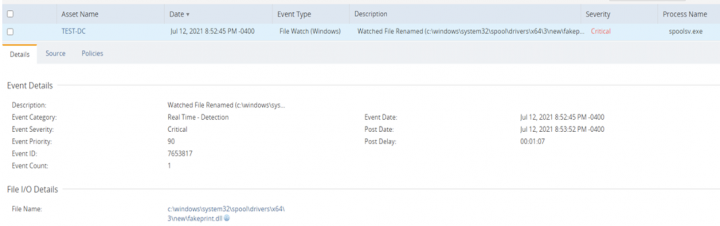
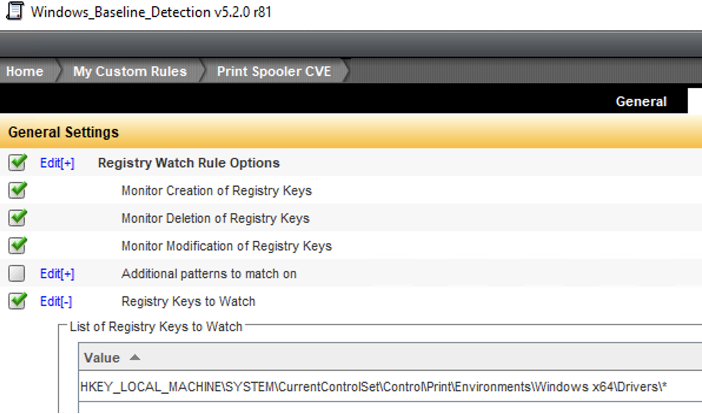
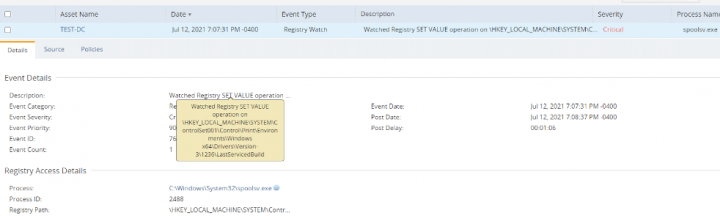
DCS Monitoring customers can use Host Intrusion Detection System (IDS) to monitor and trigger alerts for any indicator of compromise. Attacks targeting CVE-2021-1675 and CVE-2021-34527 vulnerabilities will result in malicious DLLs being written to the Spooler directories %systemroot%\system32\spool\drivers\x64 and modification of the Spooler registry keys under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Print\Environments\Windows x64\Drivers. Below is an example to create custom DCS IDS Filewatch rule to monitor real time changes to %systemroot%\system32\spool\drivers\x64\*.dll and DCS IDS Registry watch rule to monitor HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Print\Environments\Windows x64\Drivers\*
DCS Email Alerts triggered by prevention and detection events, can be configured to send notifications directly to your inbox, providing full visibility into possible acts of intrusion.
Patching is a painful and costly multi-step process for enterprises, with unexpected downtime of mission critical servers leading to lost productivity and business impact. While timely patching is important for effective vulnerability management, the default hardening posture offered by Symantec Data Center Security provides confidence to administrators that their systems and applications are well protected on day 0 from threats until patches are available and are ready to apply.

Symantec Data Center Security Provides Zero Day Protection
Keeping your Microsoft Exchange servers protected








We encourage you to share your thoughts on your favorite social platform.