How to Achieve Highly Effective Sandboxing
A comprehensive multilayered strategy is essential
Sandboxing is an essential element of cyber security strategy. The ability to isolate, examine and if necessary, detonate a file suspected to contain malware often spells the difference between protected data and a disastrous breach. But there is a big difference between simply having a sandbox in your defensive arsenal and implementing sandboxing technology in a highly effective way. For a sandbox to be highly effective, it must:
- Reach rapid and accurate verdicts regarding the safety of files.
- Run efficiently.
- Isolate and detonate a wide range of malware.
Sandboxing Pitfalls
Even organizations that do a good job at protecting themselves sometimes fail to get the most out of their sandboxes. The main reasons: Sandboxes can be slow and inefficient. A defensive strategy that forwards too many files to a sandbox will degrade network performance, erode user productivity and increase costs. Very simply, you don’t want to sandbox every suspect file that comes into your organization. At the same time, you don’t want to send a questionable file into your enterprise and inspect it later. If the file turns out to be malicious, you’ll have to remediate its impact on your organization, which will cost extra time and effort.
Better Sandboxing
How to overcome these pitfalls? The best approach is to winnow down the number of potentially malicious files that go into the sandbox using methods to catch easily identified malware, so that your incident response team is not overwhelmed with thousands of files that require manual inspection. Such a filter-funnel strategy will protect your organization from unnecessary costs and slow performance, while providing effective cyber security protection.
This is exactly how we have implemented sandboxing with Symantec, a division of Broadcom (NASDAQ: AVGO), Content Analysis System (CAS). CAS is a multilayered approach to threat protection that is integrated into our product line and in our opinion fits within Gartner’s Secure Access Service Edge (SASE) framework.* (Click here for more on SASE and Symantec's implementation of it) CAS only sends files to the sandbox when earlier, less process intensive steps do not reach a verdict with regard to the file’s safety. Here’s an example of how CAS enabled highly effective sandboxing at a Fortune 20 company:
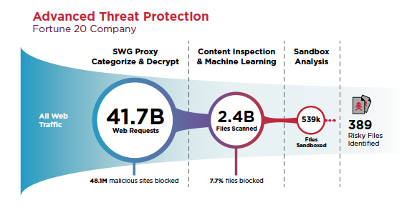
Facing 41.7 billion web requests over 30 days, the company deployed Symantec Secure Web Gateway (SWG) technology, which blocked 48 million malicious sites. Meanwhile, 2.4 billion files were sent to CAS for deeper inspection. Of those files, 539,000 ended up in the sandbox, of which, only 389 risky files – compare that to an average of 4,000 events reported to the SOC in previous months before CAS was deployed – were identified for analysis by the company’s incident response team.
Layer By Layer
By blocking a large number of potentially malicious files from known malicious website, our high-performance on-premises SWG appliances, ProxySG and Advanced Secure Gateway (ASG), play an indispensable role in limiting the number of unknown files that are forwarded to CAS for centralized, deep inspection.
CAS inspects files and compares them to massive hash reputation blacklist and whitelist databases. Bad files are blocked; good files are allowed, and unknown files are subjected to static code and machine learning analysis. Malicious files are again blocked, while files that are still unknown are subjected to analysis by as many as two separate anti-malware engines (including Symantec's and some of its top competitors). Using the signature databases of two engines increases the likelihood of recognizing malicious files.
Content that is still unknown is sent to the sandbox, which is either built into the CAS implementation or available via the cloud. Our sandbox implements both emulation and virtualization, a hybrid approach that delivers the benefits of both methods: Emulation represents “bare metal” systems to quickly catch threats; virtualization exposes threats that are targeting your specific OS environment. You can create your own customized OS images to identify malware that targets just your unique environment, eliminating a lot of false positives.
Our detection pattern library detects targeted and single-use malware, without relying on signature-based detection. Meanwhile, static code and YARA rule analysis performs file fingerprinting, detects packers, analyzes strings and uses textual and binary patterns to identify and classify malware samples.
Security Operations Center teams can view all this activity through clear and concise reports and study malware screenshots, even as they rapidly eradicate identified threats across the enterprise.
In addition, our technology analyzes files for sandbox avoidance characteristics, including sleeps designed to wait out sandbox analysis and stealth mode files that attempt to detect an artificial analysis environment. We also include a Ghost User plugin that thwarts interactive malware by simulating user behavior. Suspect files are withheld from the user while a safe verdict is rendered, preventing patient zero infections.
Security Operations Center teams can view all this activity through clear and concise reports and study malware screenshots, even as they rapidly eradicate identified threats across the enterprise. To the user, all this is swift and imperceptible.
By taking a centralized approach and applying multiple layered discovery techniques, we are able to reach rapid and accurate verdicts, work efficiently and isolate and detonate a wide range of malware. It’s highly effective sandboxing that will keep your organization safe from threats, while enabling your employees to be highly productive.









We encourage you to share your thoughts on your favorite social platform.